System Configuration
After installation the system needs to be configured to allow successful message communication between business partners. This section discusses the FMC and the various configuration settings in detail.
Prior to invoking the management console to configure the system ensure that the server keystore containing private and public keys are created as described in the Section called Generating a Private and Public key (Certificate) in the Chapter called Installation, and that the FMS server is running with the administration interface listening for connections (default).
Admin User Creation
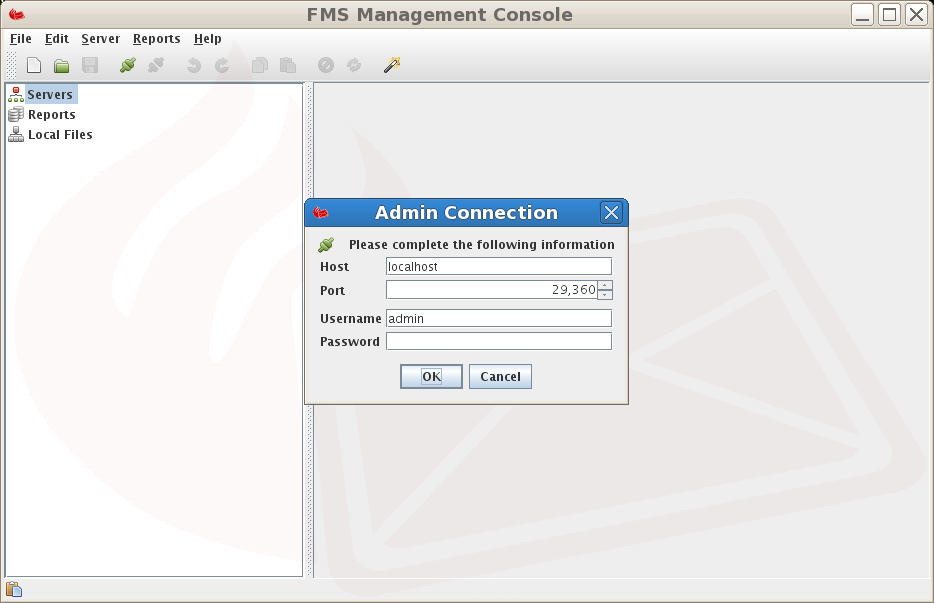
The FMC connects to the server over a secure authenticated connection. The default user is admin. The password must be created in file user.cfg on the machine on which the server is installed prior to connecting to the FMS server. This is done as follows
Windows
Open a new command console in windows and navigate to the FMS configuration directory.
\cd "\Program Files"\FMS\cfg\
Invoke the adduser.exe utility with the username as the argument as follows
\..\bin\adduser admin
Enter the user password, and again to confirm.
Repeat the above steps to reset a password.
UNIX and Linux
Open a console and navigate to the FMS configuration directory.
\cd /home/fms/
Locate and invoke the jar file fms_connections.jar with adduser and the username as the argument in the configuration directory.
\java -jar /path/to/fms_connections.jar adduser admin
Enter the user password, and again to confirm.
Repeat the above steps to reset a password.
Admin User Deletion
Delete a user by using a text editor to remove the line containing the user name in the user.cfg file.
FMC
FMC is the primary administration interface for administering the FMS server. Invoke FMC as follows
- Windows
Select FMC from the Windows command menu and log in with the user and password as set using the adduser.exe utility.
- UNIX and Linux
Invoke FMC from the command line as follows
\ \[user@localhost fms]$ java -jar fms_mc.jar & \ \
Server Administration
The FMS server configuration is stored in an XML file typically called ConnectionConfiguration.xml. The configuration can be accessed either via connecting the FMS Management Console (FMC) to an FMS server or by directly editing the FMS configuration file using a standard text editor and the fmsconf utility as described in section the Section called fmsconf Server Configuration Utility in the Chapter called FMS Tools and Utilites.
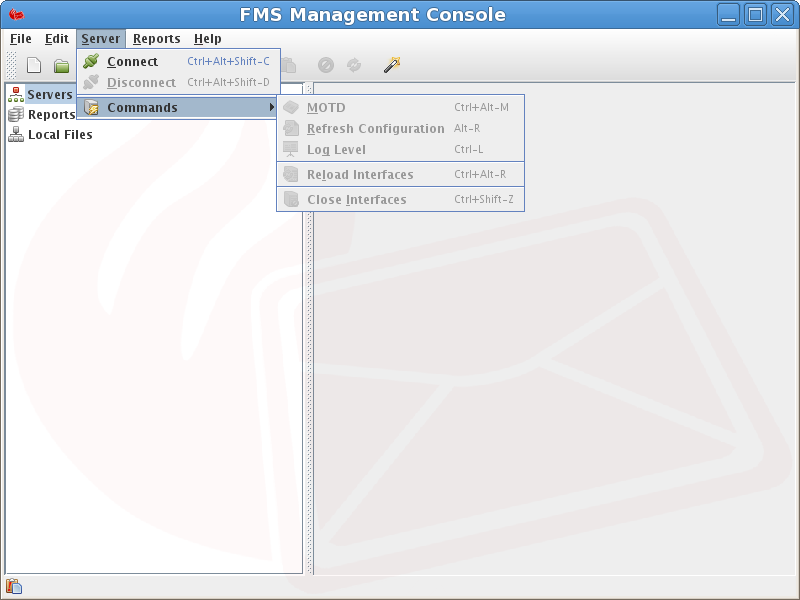
Command Descriptions:
MOTD
View the Message Of The Day as set in the administration interface.
Refresh Configuration
Reload the Configuration file but do not reload the live connections, useful when adjusting Partner Identifiers, Processing Modes/Events and other business orientated configurations.
Log Level
Adjust the current server logging level. The previous log level will be indicated by the selected button in the list of log levels.
Reload Interfaces
Close all the current connections and reload the Interface Configuration, useful when updating port numbers, hostnames, or security requirements, refer to the Section called FMS Messaging Configuration for more information.
Close Interfaces
Close all the current interfaces. Warning: All the interfaces will be shut down, including the administration interface (excluding current sessions). A server restart will be required to re-establish the interfaces should the management console disconnect while the interfaces are closed.
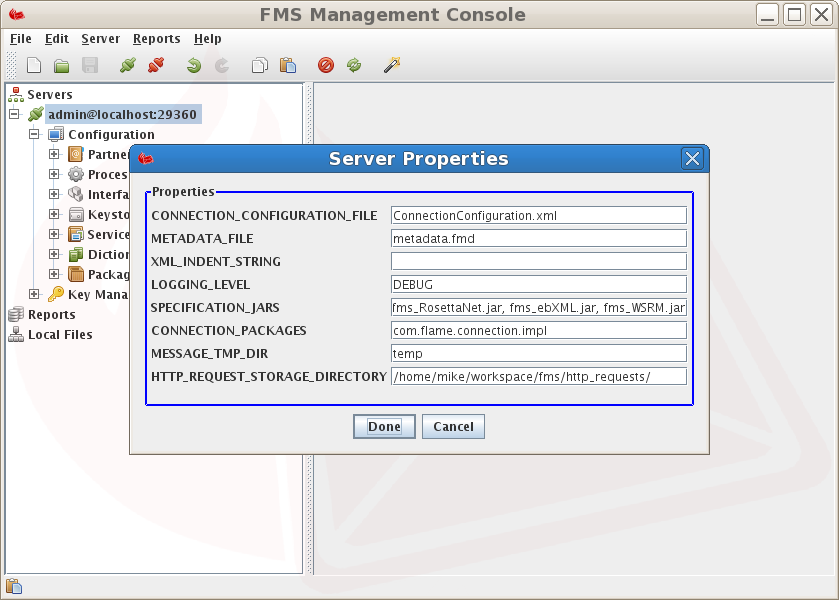
Server Settings
The server initial settings, typically stored in main.conf, can be viewed by right clicking on the Server connection node and selecting Properties.
The detail of the main configuration is as follows
- CONNECTION_CONFIGURATION_FILE
The name of the default Configuration File. This file is stored in the FMS startup directory and contains configuration settings including partner, processing mode, interface definitions, business services and protocol packagers as required for a functioning FMS.
- HTTP_REQUEST_STORAGE_DIRECTORY
Incoming requests are stored in this directory in the event of the Non-Repudiation database being unavailable.
- LOGGING_LEVEL
The starting Log Level for FMS with default set at INFO. This can be set to any one of OFF, FATAL, ERROR, WARN, INFO, DEBUG, TRACE, ALL.
- SPECIFICATION_JARS
A comma ',' delimited list of Java archives (Jars) containing specification schema (xsd), document type definition (dtd) and java class files to be referenced for entity resolution when validating/parsing XML incoming and outgoing message payloads.
The default setting is fms_RosettaNet.jar, fms_ebXML.jar, fms_WSRM.jar.
This setting is relevant in the enterprise edition when extending the available interfaces.
- XML_INDENT_STRING
XML Indent String (Spaces or \t for Tab). Defaults to two (2) spaces.
- MESSAGE_TMP_DIR
A temporary directory, automatically created, relative to the installation directory used for intermediate message payload and attachment files. The default name is temp.
- METADATA_FILE
The default FMS metadata file name (metadata.fmd) as created in the delivered-content/initiatingParty/respondingParty/message-id directory where message-id is a unique identifier for each received message ensuring that each received message has it's own associated metadata file. This XML file contains information related to delivered message payload and attachments and has the following format
\ \<?xml version="1.0" encoding="UTF-8" standalone="yes"?> \<fmd:FMSMetadataDocument xmlns:fmd="http://fms.flame.business/FMS/schema/FMSMetadataDocument"> \ <fmd:Legal> \ <fmd:Copyright>(c) Flame Computing Enterprises cc. All rights reserved</fmd:Copyright> \ </fmd:Legal> \ <fmd:To>ToPartyID</fmd:To> \ <fmd:From>FromPartyID</fmd:From> \ <fmd:ConversationID>123</fmd:ConversationID> \ <fmd:Service>A06</fmd:Service> \ <fmd:Action>http://docs.oasis-open.org/ebxml-msg/as4/200902/action</fmd:Action> \ <fmd:MessageID>739cdd60-5d45-4132-a43e-48226a4ba383@domain.com</fmd:MessageID> \ <fmd:ProcessingMode>AS4-ENTSOG-PROD</fmd:ProcessingMode> \ <fmd:Event>ReceiveMessage</fmd:Event> \ <fmd:ToRole>ZSH</fmd:ToRole> \ <fmd:FromRole>ZSO</fmd:FromRole> \ <fmd:AgreementRef>ThisAgreement</fmd:AgreementRef> \ <fmd:Timestamp>2019-05-09T15:57:46Z</fmd:Timestamp> \ <fmd:MessagePayloads> \ <fmd:Payload> \ <fmd:MimeContentID>739cdd60-5d45-4132-a43e-48226a4ba383@domain.com</fmd:MimeContentID> \ <fmd:MimeContentType>application/xml</fmd:MimeContentType> \ <fmd:Location \ >/home/fms/delivered-content/FromPartyID/ToPartyID/739cdd60-5d45-4132-a43e-48226a4ba383@domain.com/20190509175746537.xml \ </fmd:Location> \ </fmd:Payload> \ </fmd:MessagePayloads> \</fmd:FMSMetadataDocument> \ \
FMS Messaging Configuration
After a Business to Business (B2B) Messaging Agreement has been proposed the messaging configuration settings in accordance with the messaging protocol and partner agreements must be defined in order to receive and send B2B Messages.
Messaging configuration details may be configured using the FMC or directly using a text editor in the server ConnectionConfiguration.xml file.
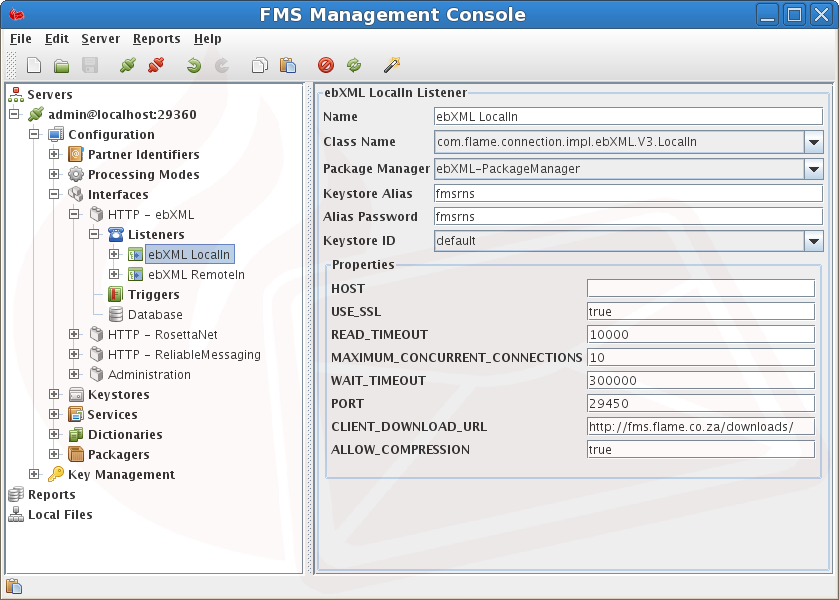
The Interface Configuration node of the FMC enables a fast and efficient way of configuring FMS interfaces. This configuration can also be performed manually by editing the file ConnectionConfiguration.xml, note that this is only recommended for advanced administrators.
New Configurations are created by selecting the New toolbar button and clicking on the New Interface option. This is only necessary for advanced customisation when adding a new protocol to FMS. Typically this is not required because the default interfaces can simply be edited. The security and database settings can be configured on a per Interface Configuration basis as per the above configuration screen shot should these be required. The Interface security level sets a minimum security level for all messages sent using this interface. Note that higher values will override Processing Mode Event Security level settings.
After the server has been started or initialised, all the enabled listener/sender configurations will be populated with default values. This screen is accessible by selecting the node for each listener/sender.
Each connection has an association to a Packager Configuration Identifier. This allows message transformation by switching between Transport Specifications such as RosettaNet to ebXML.Partner Identifier Configuration
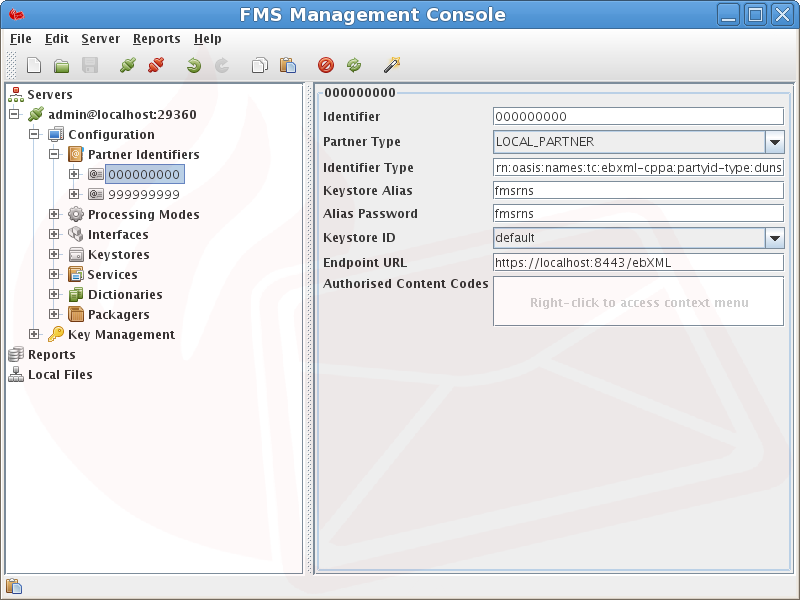
A mapping of a Partner Identifier (eg. DUNS number) to other relevant partner information needs to be created for use within the system. A default local and remote partner is automatically created by the system on startup. These should be modified according to requirements.
Create or modify an existing Partner Identifier entry by selecting New from the main menu or toolbar. Select New PartnerIdentifier. Complete the required information as follows and select Save to finalise the changes.
Identifier - The actual value, or name, of the partner identifier. The partner identifier on the local side (producer) must correspond with the partner identifier on the remote side (consumer) and vice versa.
Partner Type - The type of the partner identifier being either a LOCAL_PARTNER or REMOTE_PARTNER.
Identifier Type - The type of the partner identifier (urn:oasis:names:tc:ebxml-cppa:partyid-type:duns is used in this example). The type must match the type of the PartyID in the PartyInfo section of the CPA if used with the ebMS specification.
Keystore Alias - The Keystore Alias entry stores an Alias name in the Keystore referring to a remote partner's public certificate and the local partners private key. The public key is used to encrypt a message to be sent to the corresponding remote partner where it will be decrypted using the private key. The local partner private key is used to generate digital signature which may be attached to the message[s] and/or to the envelope containing the set of messages and optional attachments. The remote partner MSH uses the local partner public key to verify the signatures.
Alias Password - A password is required if the above alias refers to a Private Key and is used to retrieve the key during envelope and message signing and message decryption.
Keystore ID - The reference to a KeyStore from the server configuration which contains the above Private and/or Public Keys.
Partner mailBox ID - the optional configurable inbound message mailbox for local partners, LOCAL_PARTNER, and outbound message mailbox for remote partners, REMOTE_PARTNER. The mailBox setting will override the interfaceConfig.deliveredContent directory.
Mailbox directories starting with the directory separator will be treated as absolute. Directories starting without a directory separator will be saved in the FMS installation directory.
Mailbox directories may either be explicit directory names or customised using the following variables determined from inbound messages for local partners.
$toPartner - message to partner identifier with any preceding URI elements removed to ensure a consistent directory structure.
$fromPartner - message from partner identifier with any preceding URI elements removed to ensure a consistent directory structure.
$messageID - message identifier with any preceding URI elements removed to ensure a consistent directory structure.
$conversationID - message conversation identifier with any preceding URI elements removed to ensure a consistent directory structure.
$service - message service with any preceding URI elements removed to ensure a consistent directory structure.
$action - message action identifier with any preceding URI elements removed to ensure a consistent directory structure.
Endpoint URL - The Endpoint URL entry stores the endpoint URL of the partner. This being the URL of the remote service that the partner will be invoking. This entry is used in the send or response action during asynchronous service interaction with a remote partner service.
The actual endpoint used depends on several conditions being as follows
- Processing Mode CPP/A Agreement
The endpoint used will be as per the CPP/A agreement value in PRODUCTION mode for the ebXML specification if the processing mode agreement configuration setting is defined.
- Processing Mode Event Endpoint
The endpoint defined in the processing mode event will be used if no overriding processing mode CPP/A agreement in PRODUCTION mode is defined.
- Partner Endpoint
The endpoint defined for the partner will be used if neither the processing mode event configuration setting is defined nor the CPP/A agreement value in PRODUCTION mode is defined.
Authorisation List - The section Authorisation List stores a list of Schema Codes. A client will be restricted to only send items in this authorisation list. If the list is empty then no restrictions exist.
Partner Type - This is an enumeration of the following values {REMOTE_PARTNER, LOCAL_PARTNER, PULL_PARTNER}.
REMOTE_PARTNER - Defines that this server IS NOT responsible for this Partner Identifier and any incoming messages destined for this Partner Identifier must be delegated to the responsible endpoint URL.
LOCAL_PARTNER - Defines that this server IS responsible for this Partner Identifier and any incoming messages for this Partner Identifier will be stored locally for retrieval at a later stage.
PULL_PARTNER - The same as LOCAL_PARTNER, however, the message is stored in a form in which the Partner can perform a Pull Request for retrieval.
Triggers - A list of triggers associated with this PartnerIdentifier, refer to the Section called Triggers for more information.
Processing Modes
Processing Modes (as defined by the ebMS Specification) provide a centralized configuration for business messages. Processing Modes consist of the following
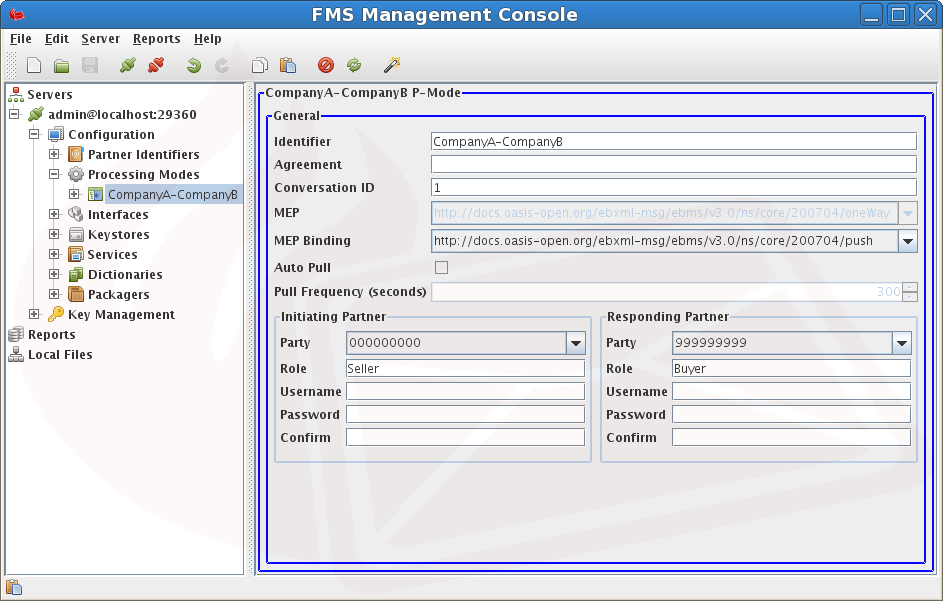
General section - Contains the message pattern, CPA configuration, and partners involved in this processing mode.
Events section - Defines the endpoint of a message, payload profiles, and other information.
Protocol - Contains information for the endpoint, http compression, and message retry configuration.
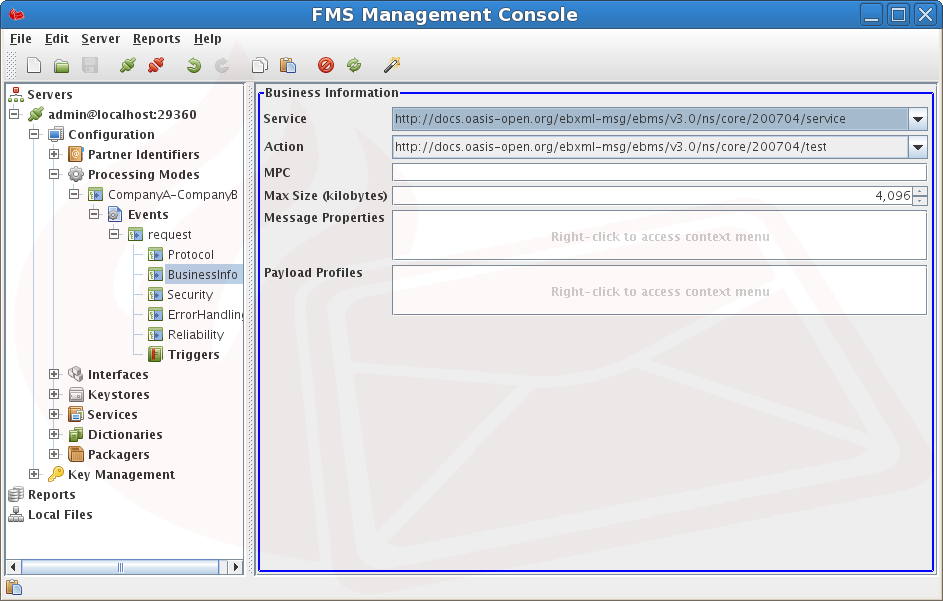
Business Information - Business centric information such as the Service and Action for this message sequence.
Security - Security information including digital encryption/signatures, and UsernameToken management.
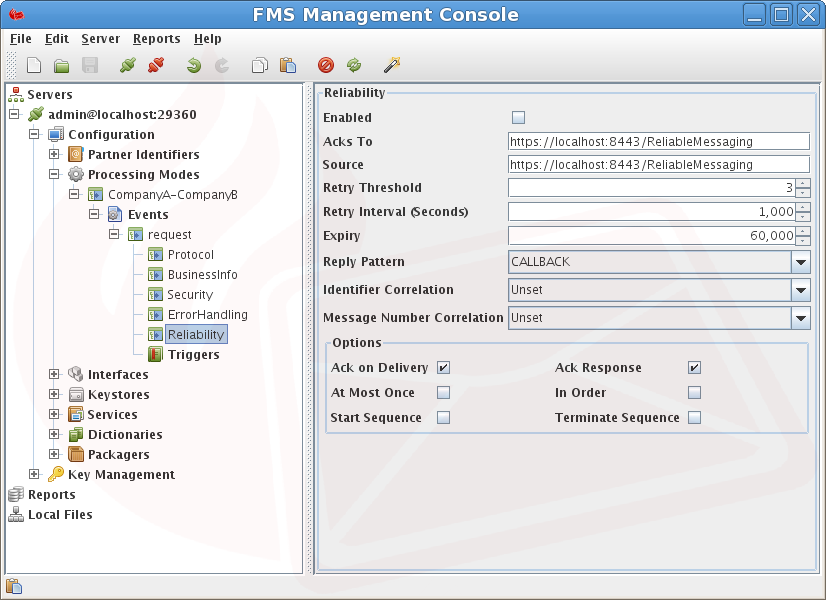
Reliability - WS-ReliableMessaging configuration.
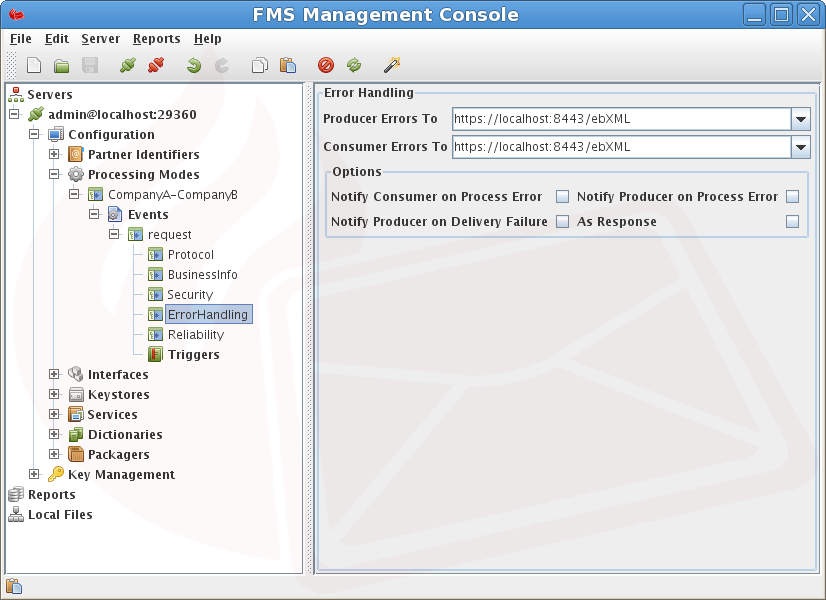
Error Handling - Who and where to send error messages to.
ProcessingModes - General Configuration
Identifier - A unique identifier for this ProcessingMode, MUST NOT contain spaces and consists of ONLY alpha-numeric characters and hyphens '-'.
Agreement - A URL pointing to a Collaboration Protocol Agreement CPA.
Conversation ID - This element is a string identifying the set of related messages that make up a conversation between Parties.
Message Exchange Pattern (MEP) - This item is not directly configurable since it is defined by the event count in this processing mode.
Message Exchange Pattern Binding - Dependant on the MEP above, if the MEP is OneWay then the MEPBinding may be one of {PUSH, PULL}, however if the MEP is TwoWay then the MEPBinding may be one of {PUSH-AND-PUSH, PUSH-AND-PULL, PULL-AND-PUSH, PULL-AND-PULL, SYNC}. SYNC is only usable if a synchronous trigger is used on receipt of an incoming message.
Party - A dropdown list of Partner Identifiers for defining the respective party for initiating or responding in this ProcessingMode.
Role - The role of the party in this ProcessingMode
Username - The username to use for UsernameToken authentication.
Password - The password to use for the supplied username. Note that confirmation of passwords will need to be performed when adjusting this value.
ProcessingModes - Event
An Event is defined as an action in which a message is sent from the initiating party to the responding party (in the first event). The parties are swaped for each subsequent event, i.e. the initiating party in the second event will temporarilly be receiving messages from the responding party.
Identifier - A unique identifier for this ProcessingMode Event, MUST NOT contain spaces and consists of ONLY alpha-numeric characters and hyphens '-'.
Event - Protocol
Defines protocol-related parameters necessary for interoperating, that are associated with a particular message of the MEP.
Identifier - A unique identifier for this ProcessingMode Event, MUST NOT contain spaces and consists of ONLY alpha-numeric characters and hyphens '-'.
Event - Business Information
Defines the business profile of a user message in terms of business header elements and their values (e.g. Service, Action) or other items with business significance (payload profile, MPC).
Event - Security
Defines the security level expected for the message in the exchange, and provides related security context data.
Event - ReliableMessaging
Defines the reliability contracts and their parameters, applying to the message in this Event.
Event - ErrorHandling
Defines the mode of handling and of reporting of errors associated with the message in this Event.
Messaging Security
B2B Messages can be secured using message signing and/or encryption of various elements of both inbound and outbound messages. This section provides the necessary detail of how messages may be sigined and or encrypted.
Digital Signatures
A digital signature is a form of authentication in which message elements such as the message body is digitally signed by a private signing key. When a message is received the receiving agent verifies the digital signature eithe with the enclosed public key, or using an external saved copy of the public key against the various signed message elements. If this verification fails the message will not be accepted since it implies that the original message was tampered with during transmission. Message signing can be configured in the relevant connection configuration as detailed in the Section called FMS Messaging Configuration. Refer to the Section called Certificate Configuration in the Chapter called Installation for information on configuring private and public keys.
Encryption
Encyption involves retrieving the recipient's public key (certificate) and encrypting the message content against it. The recipient then uses their private key to decrypt the message. This 'swopping' of certificates normally takes place when obtaining or creating a certificate as discussed in the Section called Certificate Configuration in the Chapter called Installation.
A number of steps need to be taken to ensure that encryption will take place. These include the following
The unrestricted Java policy files need to be installed to ensure unrestricted algorithm strength used for encryption. This can be achieved by copying the file local_policy.jar from the installation directory to the $JAVA_HOME/lib/security/ directory. The default policy file enforces a keystrength unsuitable for encryption with FMS.
A mapping of recipient DUNS number to Keystore alias needs to be assigned for encryption purposes. This is achieved by creating a PartnerIdentifier section by providing focus to the Partner Identifier list and clicking the Add button. Complete the required information and click Save to finalise the changes. Refer to the Section called Partner Identifier Configuration.
Package Manager Configuration
Additional messaging specifications in the form of Package Managers are supported by FMS. These package managers MUST be configured in the file ConnectionConfiguration.xml. The Packager Configuration section contains a simple mapping between a key name and a Java class path denoting the location of the relevant package manager in the classpath. These Package Managers can have their own configuration sections in the ConnectionConfiguration.xml file. By default RosettaNet and ebXML packaging specifications are included in FMS, refer to the Section called RosettaNet Package Configuration and the Section called ebXML Package Configuration.
RosettaNet Package Configuration
The RosettaNet Package Configuration Section is named RosettaNet-PackageManager. This section contains RosettaNetTM specific options such as GLOBAL_USAGE_CODE. GLOBAL_USAGE_CODE can be one of two values being Test or Production.
As well as:
Description of the RosettaNet Package configuration options:
DELIVERY_HEADER_DATE_FORMAT - The Java based date/time format for use within the packaged RosettaNet DeliveryHeader.
DELIVERY_HEADER_PATH - A Class path to the JAXB created class bindings for the RosettaNet Specification DeliveryHeader Schemas.
DELIVERY_HEADER_TIMEZONE - The Timezone to adjust the current server time to.
EXCEPTION_PATH - A Class path to the JAXB created class bindings for the RosettaNet Specification Exception Schemas.
GLOBAL_ADMINISTERING_AUTHORITY_CODE - Instance from set of codes identifying an administrating authority.
INITIATING_PARTNER_IDENTIFICATION_DOMAIN - The type of Partner Identifier to be used (For example: DUNS)
IS_SECURE_TRANSPORT_REQUIRED - Affirmative (Yes/No) value indicates that the next hub must transmit this message securely.
PREAMBLE_PATH - A Class path to the JAXB created class bindings for the RosettaNet Specification Preamble Schemas.
RECEIPT_ACKNOWLEDGMENT_PATH - A Class path to the JAXB created class bindings for the RosettaNet Specification ReceiptAcknowledgement Schemas.
RECEIVER_IDENTIFICATION_DOMAIN - The type of Partner Identifier to be used (For example: DUNS)
ROSETTANET_HEADER_NAMESPACE_AWARE - Boolean (true/false) value for use during parsing of RosettaNet headers to define XML Namespace awareness.
ROSETTANET_HEADER_VALIDATION - Boolean (true/false) value enabling/disabling RosettaNet header validation.
SENDER_IDENTIFICATION_DOMAIN - The type of Partner Identifier to be used (For example: DUNS)
SERVICE_HEADER_PATH - A Class path to the JAXB created class bindings for the RosettaNet Specification ServiceHeader Schemas.
SERVICE_MESSAGE_STANDARD - The standard with which the Service Content MUST be compliant.
SERVICE_VERSION - The version of the standard with which the Service Content MUST be compliant.
STANDARD_VERSION - Identifies the version number of the standard (RNIF Version).
ebXML Package Configuration
The ebXML Package Configuration Section is named ebXML-PackageManager.
Description of the ebMS Package configuration options:
CPA_TIME_TO_LIVE - The lifetime in seconds that the Collaboration Protocol Agreement should live for before an updated copy is retrieved from the provided URL.
CPPA_CORE - A Class path to the JAXB created class bindings for the CPP/A Specification Schemas.
DELIVERY_HEADER_DATE_FORMAT - The Java based date/time format for use within the packaged ebXML SOAP envelope.
DELIVERY_HEADER_TIMEZONE - The Timezone to adjust the current server time to.
EBMS_CORE - A Class path to the JAXB created class bindings for the ebXML V3 Specification Schemas.
ENCRYPTED_ELEMENTS - A comma delimited list of elements appearing in the Request SOAP header that should be encrypted.
ENCRYPTION_CANONICALISATION_ALGORITHM - Web Services Security specific setting.
ENCRYPTION_KEY_ALGORITHM - Web Services Security specific setting.
ENCRYPTION_SYMMETRIC_KEY_ALGORITHM - Web Services Security specific setting.
RECEIPT_ENCRYPTED_ELEMENT - A comma delimited list of elements appearing in the Receipt SOAP header that should be encrypted.
SIGNAL_CORE - A Class path to the JAXB created class bindings for the ebBP Signal Specification Schema.
SIGNATURE_ALGORITHM - Web Services Security specific setting.
SIGNATURE_CANONICALISATION_ALGORITHM - Web Services Security specific setting.
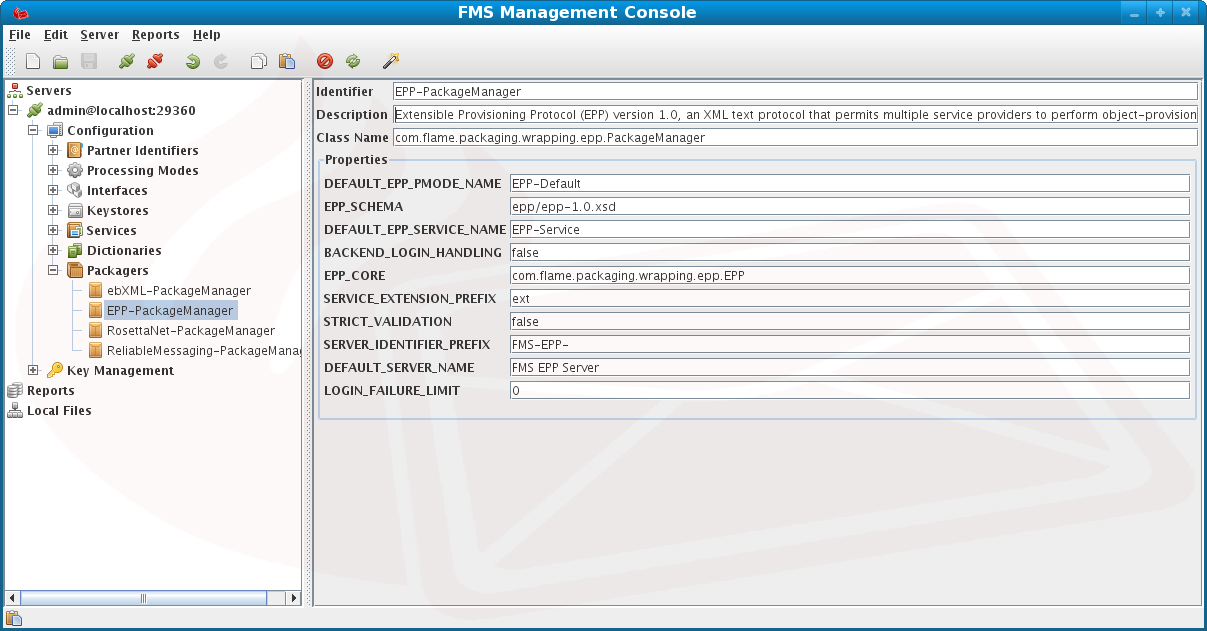
EPP Package Configuration
The EPP Package Configuration Section is named EPP-PackageManager.
Description of the EPP Package configuration options:
DEFAULT_EPP_PMODE_NAME - The provided default Processing Mode identifier that the EPP specification should use when utilizing backend authenticaton of client identifiers. The Processing Mode contains default values required for message storage and transmission.
EPP_SCHEMA - The path to the EPP XML Schema, this path is prefixed by the SCHEMA_DIRECTORY system variable.
DEFAULT_EPP_SERVICE_NAME - The provided default Service that will be used when generating EPP Greetings, this service may be extended or customized according to the Listener used.
BACKEND_LOGIN_HANDLING - When set to 'true' a trigger will be invoked to perform backend login authentication. This trigger will be invoked with a METHOD argument (set to 'login') in the Custom Arguments of the specified trigger. Note that when using an Embedded Trigger the METHOD argument is set as a variable.
EPP_CORE - A Class path to the JAXB created class bindings for the EPP Schemas.
SERVICE_EXTENSION_PREFIX - A string prefix used to differentiate internal from external Commands and/or Objects within the EPP Specification. When the Service associated Dictionary Action Code has this prefix (including a semi-colon ':', eg: 'ext:secDNS1.1') it is assumed to be an extension to EPP and treated accordingly.
STRICT_VALIDATION - This instructs the XML parser and validation system to perform a strict validation of the supplied EPP XML. The file system siblings of the above EPP_SCHEMA are located and used to validate the XML, any web references to imported Schemas will be resolved and cached so an initial load time is expected once per server instance.
SERVER_IDENTIFIER_PREFIX - A string prefix used to customize the server generated transaction identifiers when receiving an optional client transaction identifier.
DEFAULT_SERVER_NAME - The server name to be used when generating the EPP Greeting.
LOGIN_FAILURE_LIMIT - Sets the maximum number of times a login can fail before being disconnected. 0 indicates unlimited failures.